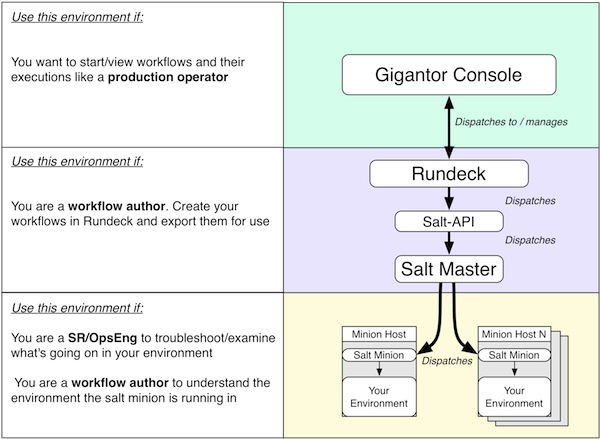
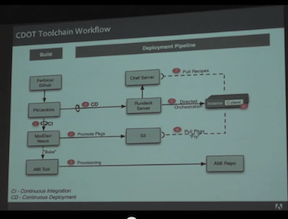
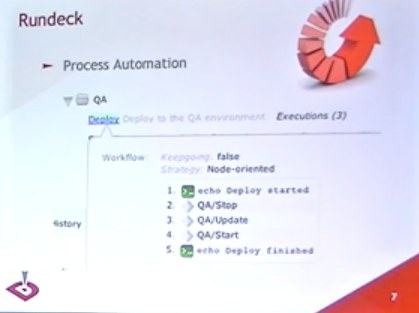
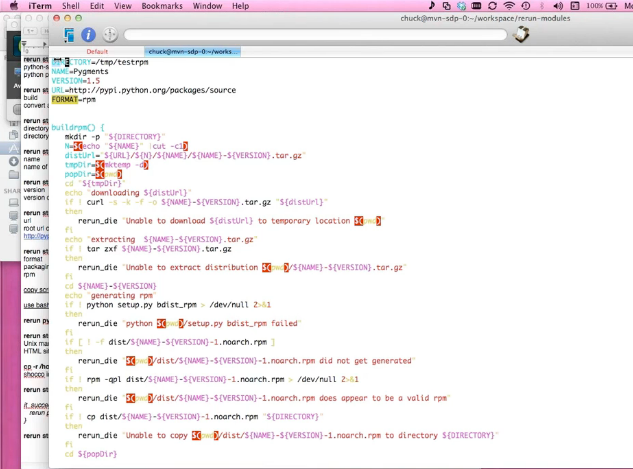
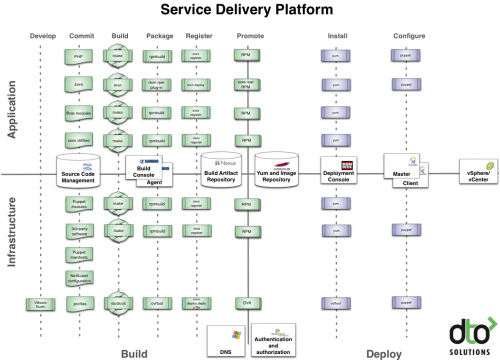
Operational excellence in IT always seems to be an illusive goal. Attempts you’ll see will often range from the “magic bullet technology” projects that rarely deliver on expectations to the addition of crushing bureaucracy that is quickly circumvented and rendered ineffectual.
With these thoughts in mind, I was leery when I picked up a copy of The Visual Ops Handbook. Wow, was I ever surprised. The Visible Ops Handbook is a compact and highly effective prescription for achieving operational excellency. It won’t get you all the way to the promised land but it will send you down the path on solid footing.

The approach is not about implementing new technology. It’s not about ivory tower bureaucracy. The Visible Ops Handbook is about bringing reliability, accountability, and predictability to your operations through a commonsense based process that doesn’t require heroic discipline or unrealistic political capital to implement.
Who should buy this book? The short answer is “everyone”. For a longer answer I’ll borrow a passage from the book’s introduction:
- Organizations that have change management processes, but view these processes as overly bureaucratic and diminishing of productivity. There must be more to change management than bureaucracy, good intentions and scarcely attended meetings.
- Organizations where, deep down, everyone knows that people circumvent proper processes because crippling outages, finger-pointing, and phantom changes run rampant.
- A “cowboy culture” where seemingly “nimble” behavior has promoted destructive side effects. The sense of agility is all too often a delusion.
- A “pager culture” where IT operations believes that true control simply is not possible, and that they are doomed to an endless cycle of break/fix triggered by a pager message at late hours of the night.
- An environment where IT operations and security are constantly in reactive mode with little ability to figure out how to free themselves from fire fighting long enough to invest in any proactive work.
- Organizations where both internal and external auditors are on a crusade to find out whether proper controls exist and to push madly for implementing new ones where they are not in place.
- Organizations where IT understands the need for controls, but does not know which controls are needed first.
Yes, they are talking about you.
It’s a short read (100 pages including several appendices), so buy one for everyone in your department. Available in paperback from Amazon or as a PDF from itpi.org.
*Note: the full title is “The Visible Ops Handbook: Implementing ITIL in 4 Practical and Auditable Steps”. In my opinion the fact that ITIL is in the title is a bit misleading. There are some sidebar discussions that draw connections between the Visible Ops process and ITIL, but this is a book about how to succeed in operations first and foremost. I suspect the ITIL connection was made for marketing reasons. Don’t let it taint your opinion before you read the book.